CIO
Towards smarter security
By: Adib C. Ghubril
What is your number one priority?
Imagine if the CIO’s job could be described with that kind of clarity. Well, as a matter of fact, it can be.
Corporate boards and the c-suite may not spend too much time thinking about information systems (unless they are an information systems company) but one thing they definitely think about, and indeed fret about, is security breaches and the persistence of cyber threats.
Regardless of whether your organization has a chief information security officer (CISO), your top priority as CIO is to protect your organization.
What follows is one approach to consider for safeguarding enterprise knowledge.
Playing the gating game in jail
A gating game is typically a contest of strategy or adventure in which participants can only proceed by solving a puzzle. Gamers must discover an artifact that unlocks a doorway or solve a riddle that reveals a pathway to the next stage. Gamers often consider this challenge a measure of their intellectual acumen and will spend hours, and indeed days, to overcome the impasse.
The idea of partitioning an area of interest and controlling flow with logical, if not physical, gates rings true in security. At the risk of suggesting a callous metaphor, a correctional facility manages the flow of inmates and personnel by granting section access in real time according to perceived conditions. Certain behaviors trigger a sequence of events that confine any possible danger by locking out the appropriate sectors.
A smart CIO could combine these two concepts to create a security system based on behavioral awareness and problem solving.
It’s not zero trust, it’s zero effort
Below is a basic outline of an email system containing a network of senders and receivers along with accompanying client-server pairs. The green boxes represent users, sending and receiving emails. The yellow bidirectional arrows depict the act of authenticating and interacting with the email client. The blue boxes represent the email client-server systems supporting these users and the blue arrows represent the interconnections in that system (note: dark blue delineates network and computing resources at the disposal of the enterprise).
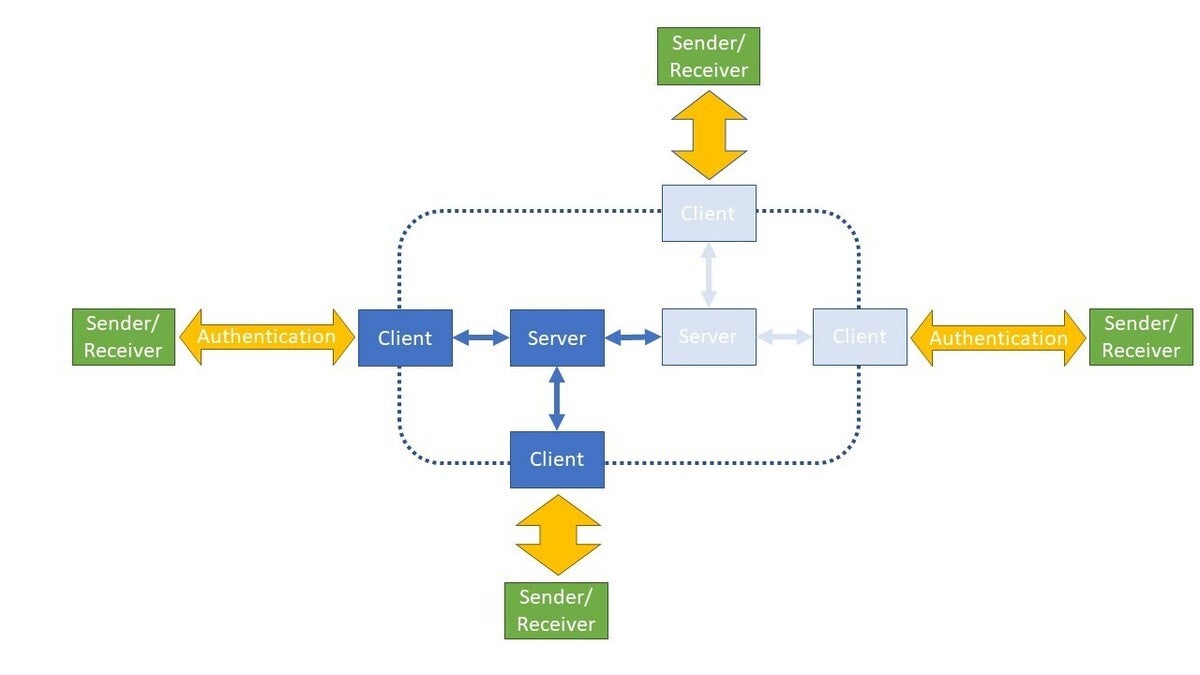
Once past the yellow arrows, a malevolent bot could essentially have its way throughout the network. And that’s what happens within an organization. Virus detection running on servers can zero-in on a problematic client, whereby the user associated with that hardware resource is dutifully informed and trained on the vagaries of social engineering, if not admonished.
Creating context-aware systems
But can the server develop a behavioral profile for each client and subsequently shut things down judiciously? What if an organization server treats every client as a user and issues authentication requests at some nominal cadence? Conversely, what if every client creates a profile of interactions with its server and with its user. Given the copious amounts of data exchanged, a machine learning algorithm running on both client and server could certainly make informed decisions about the level of cyber threat to the system.
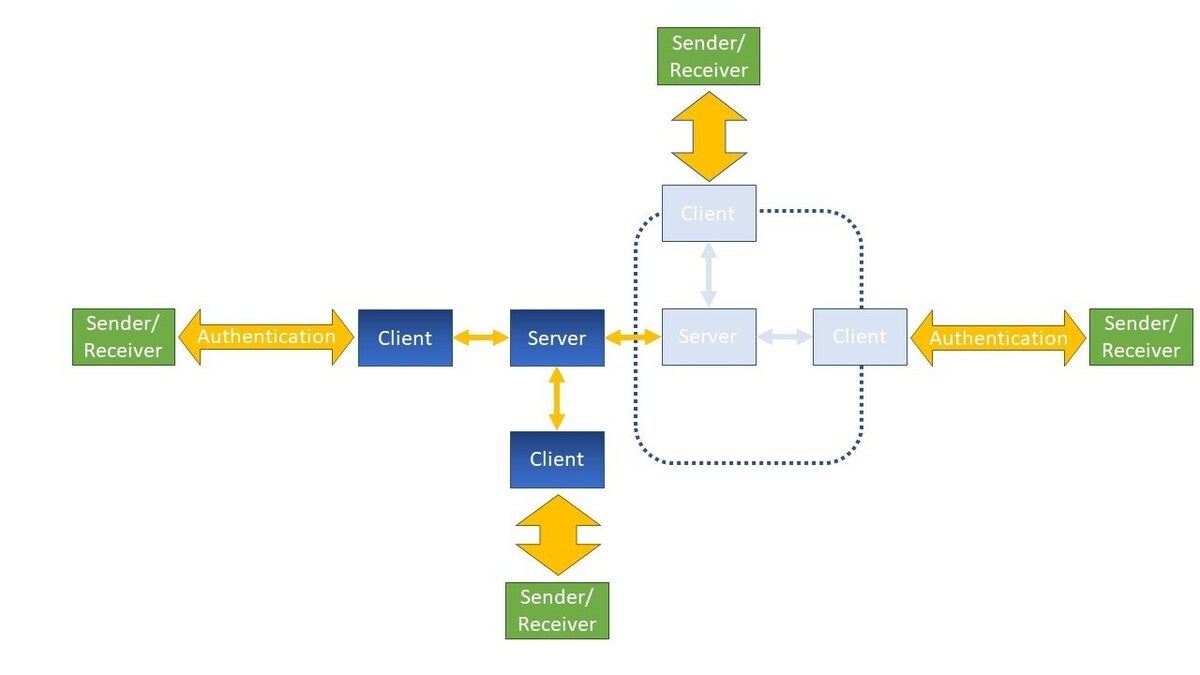
With more decision gates introduced into the network (graded coloring of the dark blue client-server network depicts on-board artificial intelligence), the area in which a virus or antagonist can freely overrun is very much reduced.

